Discover the power of the MITRE ATT&CK Framework in revolutionizing cyber threat detection and response. Our in-depth blog explores how this comprehensive knowledge base maps adversary tactics, techniques, and procedures (TTPs) to help organizations strengthen their defenses. Learn about real-world applications, such as incident response, red team exercises, and threat intelligence integration, supported by actionable insights and case studies like the SolarWinds and WannaCry attacks. Stay ahead of evolving threats by leveraging this essential tool for modern cybersecurity strategies.
Full form of MITRE ATT&CK : MITRE Adversarial Tactics, Techniques, and Common Knowledge

Table of Contents
Introduction
In the ever-evolving landscape of cybersecurity, understanding the strategies and techniques employed by attackers is critical. Imagine having a comprehensive playbook that details how adversaries operate, from initial access to exfiltration—enter the MITRE ATT&CK Framework.
Since its inception in 2013, ATT&CK has become one of the most respected and most referenced resources in cybersecurity. ATT&CK is a knowledge base of hacking techniques you can use to defend your network from cybersecurity threats. To know ATT&CK is to understand your enemy.
Created to provide a universal language for understanding and mitigating cyber threats, the MITRE ATT&CK Framework has become a cornerstone in the world of cybersecurity. Whether you’re a security analyst, incident responder, or IT professional, this framework equips you with actionable intelligence to enhance your organization’s defenses.
This blog will explore:
- What the MITRE ATT&CK Framework is and why it matters.
- Key components like tactics, techniques, and procedures (TTPs).
- Real-world applications and examples.
- How organizations can use it to improve threat detection and response.
- Emerging trends and challenges.
What is the MITRE ATT&CK Framework?
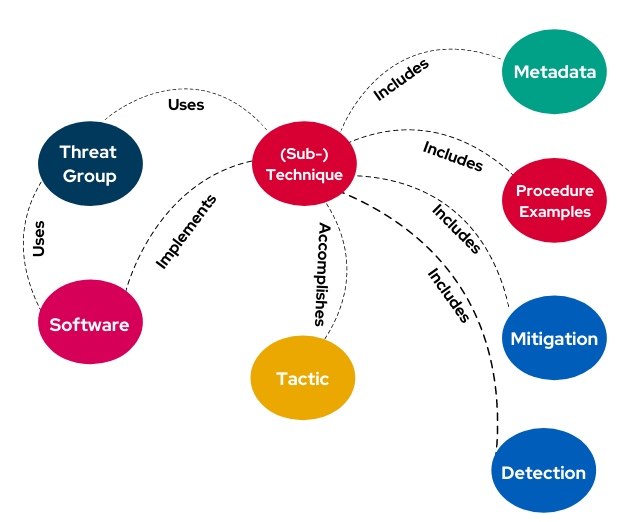
The MITRE ATT&CK Framework (Adversarial Tactics, Techniques, and Common Knowledge) is a knowledge base of adversary behaviors based on real-world observations. It categorizes cyberattack methods into tactics, techniques, and procedures, offering a structured way to analyze and mitigate threats.
- Tactics: High-level objectives or goals attackers aim to achieve, such as persistence or privilege escalation.
- Techniques: Specific methods used to accomplish these goals, like spear-phishing or exploiting misconfigured services.
- Procedures: Detailed, real-world instances of techniques used by specific threat actors.
Why is the MITRE ATT&CK Framework Important?
- Standardized Language: Enables consistent communication across teams and organizations.
- Threat Analysis: Helps identify gaps in defenses by mapping attack behaviors.
- Proactive Defense: Empowers organizations to anticipate and mitigate threats.
- Tool Integration: Widely supported by SIEMs, SOARs, and other security tools for enhanced threat detection.
MITRE Tactics: A Closer Look
The 14 tactics in the MITRE ATT&CK Framework represent the stages of an adversary’s operations, from planning to achieving their goals. Here’s a breakdown:
| Tactic | Attacker’s Objective |
|---|---|
| 1. Reconnaissance | Gather information to plan future operations. |
| 2. Resource Development | Establish resources to support their operations. |
| 3. Initial Access | Gain entry into your network. |
| 4. Execution | Run malicious code. |
| 5. Persistence | Maintain their foothold in your systems. |
| 6. Privilege Escalation | Gain higher-level permissions for broader access. |
| 7. Defense Evasion | Avoid detection by your defenses. |
| 8. Credential Access | Steal account names and passwords. |
| 9. Discovery | Understand your environment and identify targets. |
| 10. Lateral Movement | Move through your network to find valuable systems. |
| 11. Collection | Gather data relevant to their goals. |
| 12. Command and Control | Communicate with compromised systems to maintain control. |
| 13. Exfiltration | Steal data from your systems. |
| 14. Impact | Manipulate, interrupt, or destroy systems and data. |
Key Components of MITRE ATT&CK
1. Enterprise ATT&CK
Focuses on adversary behaviors targeting enterprise networks, covering operating systems like Windows, Linux, and macOS.
2. Mobile ATT&CK
Addresses techniques used to exploit mobile devices, such as Android and iOS.
3. PRE-ATT&CK (now merged into Enterprise ATT&CK)
Highlights adversary behaviors before an actual breach, such as reconnaissance and weaponization.
Real-World Examples
Case Study 1: SolarWinds Attack (2020)
- Incident: A sophisticated supply chain attack exploited SolarWinds software, compromising over 18,000 customers, including government agencies.
- ATT&CK Mapping:
- Tactic: Initial Access
- Technique: Supply Chain Compromise (T1195)
- Mitigation: Regular updates, supply chain assessments, and improved monitoring could have reduced the impact.
Case Study 2: WannaCry Ransomware (2017)
- Incident: A global ransomware attack exploiting SMB vulnerabilities affected over 230,000 systems.
- ATT&CK Mapping:
- Tactic: Execution
- Technique: Exploitation of Remote Services (T1210)
- Mitigation: Patching systems and network segmentation could have prevented propagation.
Visual and Interactive Elements
- Infographic: A flowchart mapping a typical attack using the MITRE ATT&CK Framework.
- Diagram: Visual representation of tactics, techniques, and procedures (TTPs).
- Video Tutorial: Link to a YouTube video explaining how to use the MITRE ATT&CK Navigator tool.
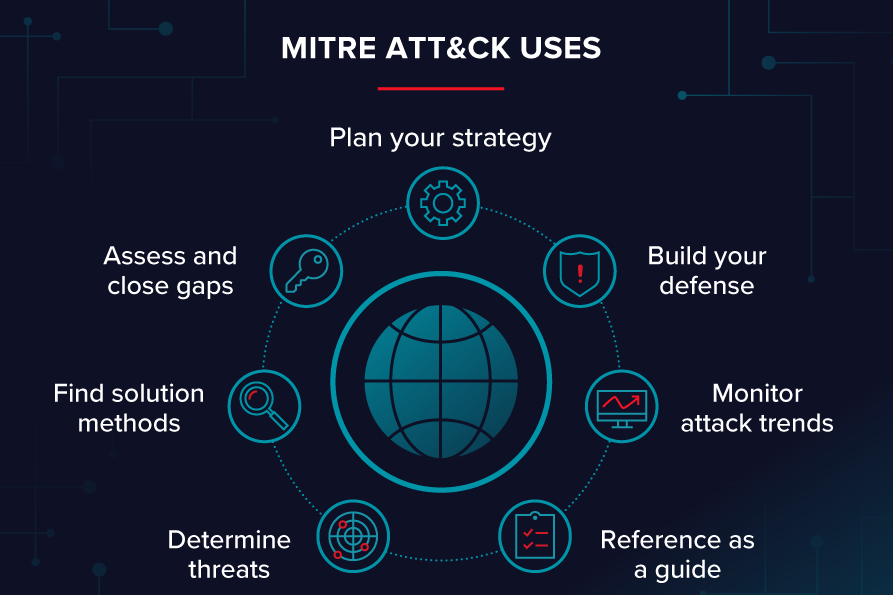
How to Use MITRE ATT&CK in Your Organization
1. Threat Detection
- Map observed attack patterns to the framework to identify ongoing threats.
- Tools like Splunk and Elastic integrate ATT&CK for advanced detection.
2. Incident Response
- Use ATT&CK to guide response strategies by understanding attacker objectives.
3. Red Team Exercises
- Simulate adversary behaviors to test the effectiveness of your defenses.
4. Threat Intelligence
- Align threat reports with ATT&CK for deeper insights and actionable intelligence.
Emerging Trends and Challenges
- Automation and AI: Integration of AI for mapping threats to ATT&CK in real time.
- Expanding Framework: Continuous updates to address new attack methods like cloud-based threats.
- Complexity: Effective use requires expertise and proper training.
- Adversarial Adaptation: As organizations use ATT&CK, attackers evolve to bypass mapped defenses.
Video links :
Conclusion
The MITRE ATT&CK Framework is not just a tool; it’s a paradigm shift in how organizations approach cybersecurity. By focusing on adversary behavior, it equips defenders with the insights needed to stay one step ahead of attackers.
Whether you’re enhancing threat detection, guiding incident response, or training your teams, ATT&CK is an invaluable resource. Start leveraging it today to strengthen your defenses and stay prepared for tomorrow’s threats.
💬 Engage with us: How are you using the MITRE ATT&CK Framework in your organization? Share your experiences or ask questions below!
Resources and References
MORE
- AI-Driven Cyber Threats: Understanding and Mitigating the Risks of Artificial Intelligence in Cybersecurity
- Quantum-Resistant Cryptography: Protecting Data in the Age of Quantum Computing 15
- Multi-Factor Authentication (MFA): Strengthening Security with Layers of Protection 14
- Zed Attack Proxy (ZAP): A Hacker’s Best Friend 13
- What is an IDOR Attack? A Beginner’s Guide to Insecure Direct Object References 12
- VAPT Demystified: A Complete Guide to Vulnerability Assessment & Penetration Testing 10
- Hackers Playbook: 15 Common Cyber attack Techniques
- 9 Career Job in Cybersecurity : A Comprehensive Guide
- How to Spot a Phishing Email : Prevent With Detailed Analysis 06
- Top 10 Cybersecurity Myths Debunked – Protect Yourself Online
- Phases of Hacking
- Mastering DVWA: Complete Guide to the Damn Vulnerable Web App for Ethical Hacking
- Web Application Penetration Testing (WAPT)
- Can you hack your wifi ?




