Phishing Email Analysis: A Comprehensive Guide to Spotting and Avoiding Scams

Introduction
Phishing attacks are a common cyber threat that involves tricking individuals into revealing sensitive information, such as passwords, credit card numbers, or social security numbers. In this blog post, we will delve into the tactics used by phishers and provide tips on how to identify and avoid these malicious emails.
Table of Contents
Email Security
- Phishing email is a type of cyberattack where a fraudulent email is sent to a victim, usually impersonating a trustworthy entity such as a bank, social media platform, or government agency, with the aim of stealing sensitive information or money.
- The email often contains a sense of urgency, prompting the recipient to take immediate action, such as clicking on a link, entering login credentials, or downloading an attachment. Phishing emails can be sophisticated and appear to be legitimate, but they are designed to trick the recipient into revealing personal information or installing malware on their computer or device.
- It is important to be cautious when receiving emails from unknown or suspicious sources and to verify the authenticity of the sender before taking any action.
Phishing Email Types
- Deceptive Phishing: This is the most common type of phishing email where the attacker impersonates a legitimate entity, such as a bank or social media platform, and asks the recipient to provide personal information or click on a malicious link.
- Spear Phishing: In this type of attack, the attacker targets a specific individual or organization, often with customized and personal messages. The goal is to gain access to sensitive information or networks.
- Whaling: This is a type of spear phishing that targets high-level executives, such as CEOs or CFOs, with the aim of stealing valuable corporate data or financial information.
- Clone Phishing: In this type of attack, the attacker creates an exact copy of a legitimate email, but with a malicious link or attachment.
- Vishing: This is a type of phishing attack that occurs over the phone, where the attacker poses as a legitimate representative of a company or organization and asks for sensitive information, such as credit card numbers or login credentials.
Sender Policy Framework (SPF)
SPF stands for “Sender Policy Framework.” It is an email authentication method designed to help prevent email spoofing and phishing attacks by verifying the sender’s authenticity.
- DNS Record Setup: The domain owner creates an SPF record in their domain’s DNS settings. This record lists the IP addresses or domains allowed to send emails for that domain.
- Sending an Email: When someone sends an email claiming to be from a specific domain, the recipient’s mail server can check if the sender is legitimate using SPF.
- SPF Check: The recipient’s mail server looks up the sender’s domain’s DNS records. The SPF record lists the authorized mail servers and IP addresses.
- IP Address Comparison: The recipient’s mail server gets the IP address of the sending server from the email’s metadata and compares it with the authorized IP addresses in the SPF record.
- Policy Evaluation: The recipient’s mail server checks if the sending server’s IP address is allowed to send emails for the domain. If it matches, the SPF check passes.
- Pass, Fail, or SoftFail: The results of the SPF check can be:
- Pass: The IP address is authorized, and the email passes the SPF check.
- Fail: The IP address is not authorized, and the email fails the SPF check. The email may be marked as suspicious or rejected.
For Details you can search : https://www.techtarget.com/searchsecurity/definition/Sender-Policy-Framework
Here is the background of how DNS works ?
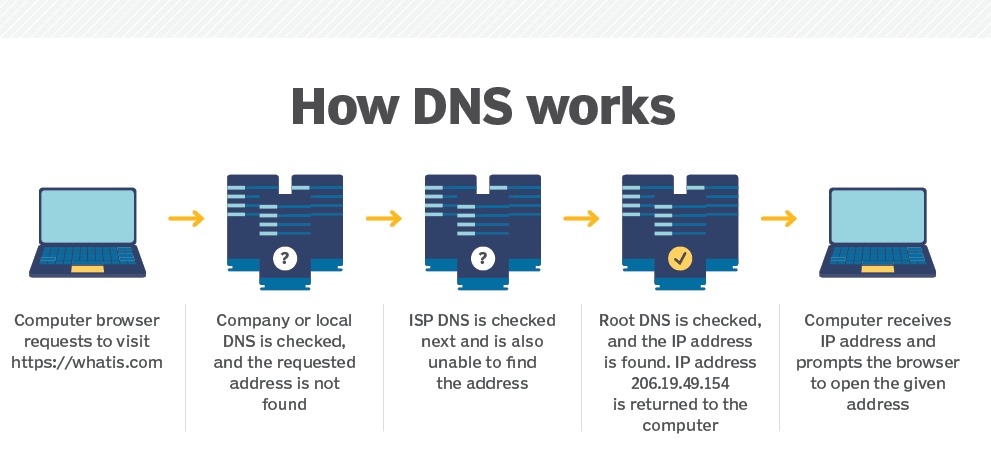
DomainKeys Identified Mail (DKIM)
DKIM is an email authentication method that helps verify the authenticity of an email and ensures it hasn’t been altered during transit. It allows the sender to digitally sign their emails using encryption so that the recipient can verify the email came from the claimed sender and that its content hasn’t been tampered with.
Here’s how DKIM works:
- Sender Signing: When an email is sent from a domain with DKIM, the sender’s mail server adds a digital signature to the email header using a private key that only the sender knows.
- Public Key Publication: The sender’s domain publishes a public key in its DNS records. The recipient uses this public key to verify the signature.
- Email Transmission: The email travels through various mail servers and relays as it makes its way to the recipient.
- Recipient Verification: When the email arrives at the recipient’s mail server, the server retrieves the public key from the sender’s DNS records using the domain in the email’s DKIM signature to verify the email’s authenticity.
Domain-based Message Authentication, Reporting, and Conformance (DMARC):
DMARC is an email authentication and reporting protocol that builds on SPF and DKIM. It enables domain owners to specify policies for how receiving mail servers should handle emails that fail SPF or DKIM checks. DMARC allows domain owners to set policies to “monitor,” “quarantine,” or “reject” emails that do not pass authentication checks. Additionally, DMARC provides reporting mechanisms that allow domain owners to receive feedback on email delivery and authentication results, helping them identify potential abuse or unauthorized use of their domain.
NOW WE PERFORMING PHISHING EMAIL ANALYSIS :
STAGE – I
Email Header Analysis and decide the whether the email header is Spoofed or not?

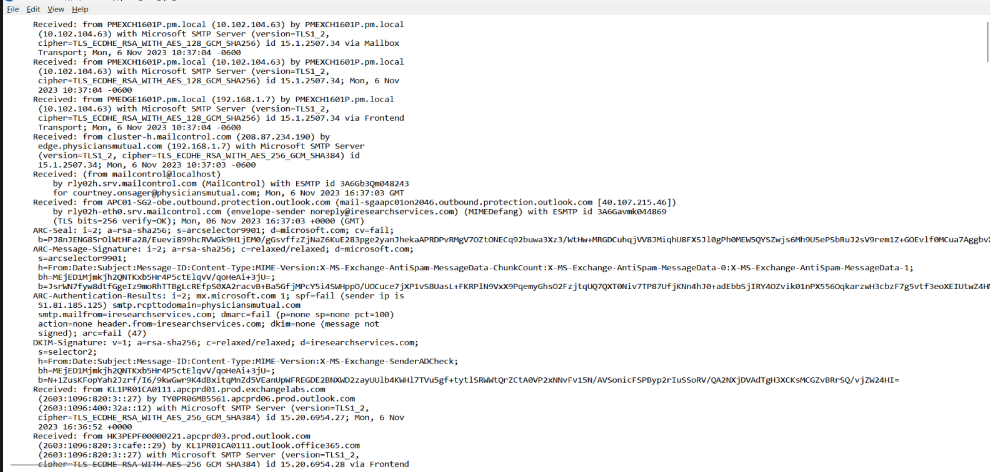
1) Open the email in thunderbird (More -> View source) and copy the source
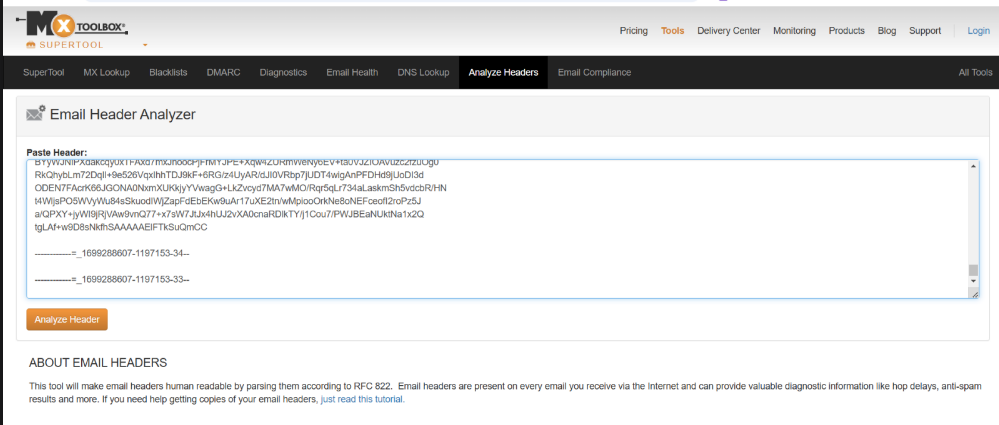
2) Open mxtoolbox.com and click on “Analyze Headers” tab
3) Paste the coped header info, click on “Analyze Header” button
Observe the following
a) SPF, DKIM, DMARC and Blacklist – Observe green and red marks

b) Verify Sender and Receiver emails, Return Path email and Deliver to email.

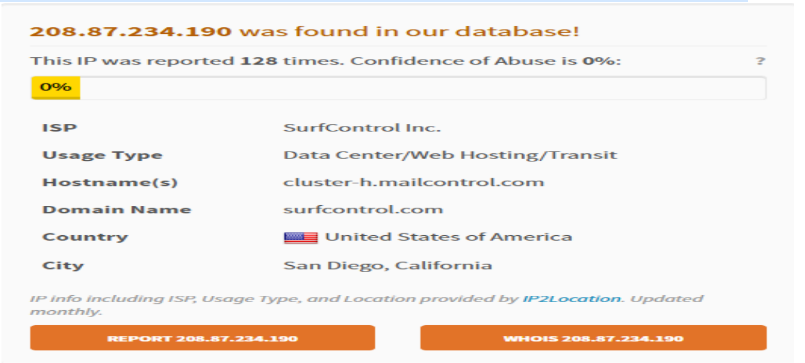
c) Check 1st “From IP address” (Private or Public)

The IP address 208.87.234.190 is a public IP address
d) Abuseipdb.com – If it is Public IP address then it will be found by abuseipdb.com
STAGE – II
Email Body analysis
1) check indicators of Urgency or fear tactics
2) check for attachments (upload to Anyrun website and analyze)

3) URL Analysis
4) websites to be uses for URL analysis – virustotal.com, sitereview.bluecoat.com, urlscan.io,
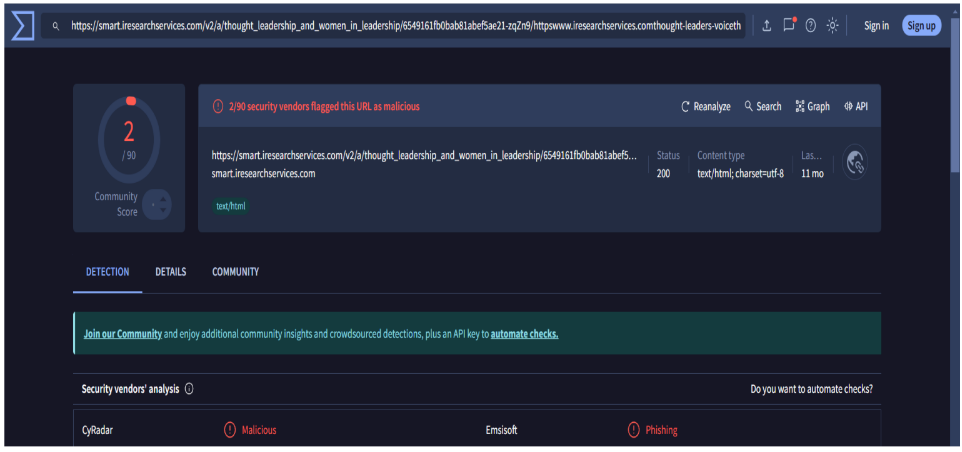
https://www.virustotal.com/gui/url/3c1586322bf324e3471522a0519b65e6c5edb14cfee427eb80c9dcae19a5acfd
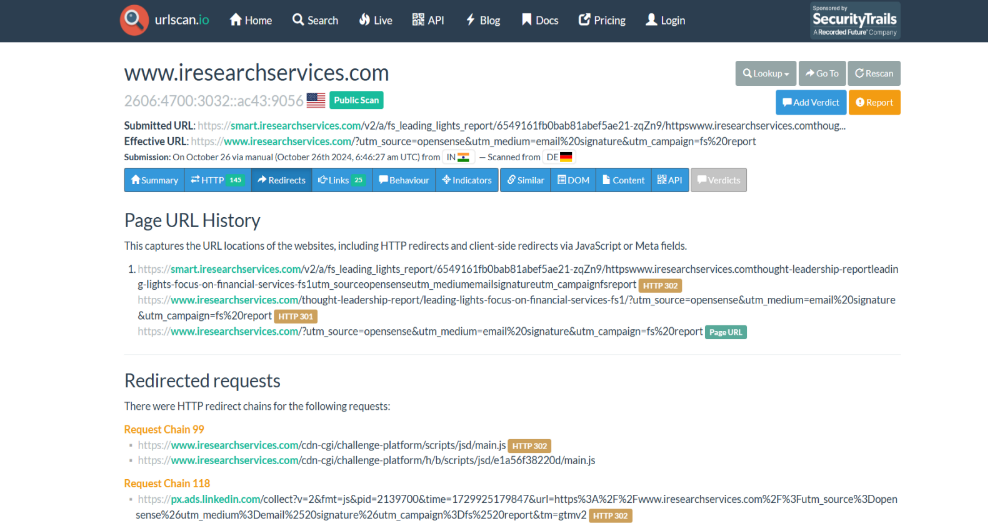
Check this websites : https://urlscan.io/result/bcd94345-9bb7-4e8f-9fce-d782f0024232/#redirects
Best Practices for Phishing Prevention
- Keep Software Updated: Install security updates to protect against vulnerabilities.
- Use Strong, Unique Passwords: Create strong, unique passwords for all your online accounts.
- Enable Two-Factor Authentication: Add an extra layer of security to your accounts.
- Be Cautious of Social Media: Avoid sharing personal information on social media.
- Educate Yourself: Stay informed about the latest phishing tactics and scams.
Conclusion
By understanding the tactics used by phishers and following best practices, you can significantly reduce your risk of falling victim to phishing attacks. Stay vigilant, be cautious, and protect yourself from cyber threats.
Optional Additional Topics:
- Phishing Kits and Dark Web Markets: Explain how phishers use pre-built tools to launch attacks.
- Mobile Phishing: Discuss the rise of phishing attacks targeting mobile devices.
- Phishing Prevention Tools: Introduce tools and techniques to help identify and block phishing emails.
- Case Studies: Analyze real-world phishing attacks to illustrate the techniques used by cybercriminals.




10 Comments