Insecure Direct Object Reference (IDOR) attacks are a critical web application vulnerability that allows unauthorized access to sensitive data. This blog explains how IDOR works, the risks it poses to businesses and users, and the techniques hackers use to exploit it. Learn how developers can detect and prevent IDOR vulnerabilities by implementing secure coding practices, proper access control mechanisms, and robust testing. Explore real-world examples of IDOR attacks and their impact, along with actionable steps to secure your applications. Whether you’re a developer or a cybersecurity enthusiast, this guide will help you strengthen your defenses against IDOR attacks.

An IDOR attack is a type of web application vulnerability that occurs when an application uses user-supplied input to directly access internal objects, such as database records or files, without proper authorization checks. This allows attackers to bypass access controls and access resources intended for other users or accounts.
Table of Contents
How IDOR Attacks Work
- User-supplied input: An attacker identifies a web application that uses user-supplied input to retrieve internal objects. This input is often in the form of a unique identifier, such as an order ID, user ID, or file name.
- Parameter modification: The attacker modifies the value of the parameter used to retrieve the object, allowing them to access objects belonging to other users or unauthorized areas of the application.
- Unauthorized access: The modified parameter is used to directly access the internal object, bypassing authorization checks. This enables the attacker to view, edit, or delete sensitive information, such as personal data, financial records, or confidential documents.
Examples of IDOR Attacks
- An e-commerce website allows users to view their order details by modifying the order ID in the URL. An attacker can access other users’ order details by changing the order ID parameter.
- A file-sharing platform allows users to access files by modifying the file ID in the URL. An attacker can access files belonging to other users by changing the file ID parameter.
Types of IDOR Attacks
These days, identifiers are more commonly found in headers or APIs than right in a user’s address bar. However, the dynamic nature of most websites means that identifiers and parameters are still heavily used in some form or another. Identifiers might include:
- URL Tampering
- Body Manipulation
- Path Traversal
1. URL Tampering
URL tampering is the simplest way to exploit an IDOR vulnerability and often requires little or no technical expertise. In this type of attack, we can simply change the value of a parameter in our web browser’s address bar.
In my college example, I changed my own student ID to that of other students, professors, and employees at the university. Tools can also be used to modify the HTTP request, but the end result is the same: the server grants some type of inappropriate access to an attacker.
I had the advantage of knowing a few of these IDs ahead of time — a real attacker would likely spend time enumerating different values and trying to discern a predictable pattern.
Below: A simple URL tampering attack might consist of changing a single parameter ID in an address bar.
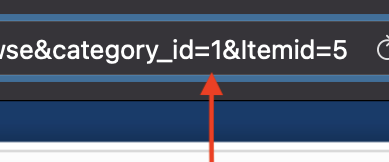
2. Body manipulation
Body manipulation is very similar to URL tampering, except that the attacker is modifying one or more values in the body of the document instead of in the URL. This can mean changing the values of radio buttons, checkboxes, or other form elements. It might also be possible to change hidden form values.
Perhaps a contact has a hidden form value that passes on the user ID for the currently logged-in account. If we can change that hidden value prior to form submission, we can make our request appear to come from a different user.
3. Path traversal
Path traversal, also called directory traversal, is a unique type of IDOR vulnerability that an attacker leverages to access or manipulate files or folders directly on the server that runs the web application. This is a level deeper than other types of IDOR attacks because it allows direct access to file system resources instead of database records. Path traversal can allow an attacker to access configuration files, discover user credentials, or even obtain a fully functional shell on the target.
Consequences of IDOR Attacks
- Confidentiality: Attackers can access sensitive information belonging to other users.
- Integrity: Data can be modified or deleted without proper authorization.
- Availability: IDOR attacks can disrupt access to critical resources or functionality.
Prevention and Detection
- Use secure object references: Instead of using user-supplied input to directly access internal objects, use indirect references or secure token-based systems.
- Implement proper authorization checks: Verify the user’s permissions and authorization before accessing internal objects.
- Validate and sanitize user input: Ensure that user-supplied input is validated and sanitized to prevent parameter modification attacks.
- Regularly test and audit applications: Identify and remediate IDOR vulnerabilities through regular testing and auditing.
- https://cheatsheetseries.owasp.org/cheatsheets/Insecure_Direct_Object_Reference_Prevention_Cheat_Sheet.html
MORE
- How SSL Certificates Authenticate and Secure Connections: Inside the SSL/TLS Handshake 11
- VAPT Demystified: A Complete Guide to Vulnerability Assessment & Penetration Testing 10
- Hackers Playbook: 15 Common Cyber attack Techniques
- 9 Career Job in Cybersecurity : A Comprehensive Guide
- How to Spot a Phishing Email : Prevent With Detailed Analysis 06
- Top 10 Cybersecurity Myths Debunked – Protect Yourself Online
- Phases of Hacking
- Mastering DVWA: Complete Guide to the Damn Vulnerable Web App for Ethical Hacking
- Web Application Penetration Testing (WAPT)
- Can you hack your wifi ?




10 Comments